Internet Protocol Security (IPSec) is an open standards framework that ensures secure and secure communications over Internet Protocol (IP) networks by using encrypted security services. The implementation of IPSec for the Microsoft® Windows® 2000, Windows XP, and Windows Server 2003 family is based on standards developed by the Internet Engineering Task Force (IETF) IPSec working group. IPSec (Internet Protocol Security) is the long-term direction of secure networking. It provides proactive protection through end-to-end security to protect against private network and Internet attacks. In communication, only the sender and receiver are the only computers that must understand IPSec protection. In the Windows 2000, Windows XP, and Windows Server 2003 family, IPSec provides the ability to protect workgroups, LAN computers, domain clients and servers, branch offices (physically remote), extranets, and roaming clients Communication between. IPSec is a set of IP security protocols established by the IPSec team of the Internet Engineering Task Force (IETF). IPSec defines security services used at the Internet layer, and its functions include data encryption, access control to network elements, data source address verification, data integrity checking, and protection against replay attacks. IPSec's security service requires support for shared key to complete authentication and/or confidentiality, and the way to manually enter the key must be supported. The purpose is to ensure interoperability of the IPSec protocol. Of course, the ability to manually enter the key is very poor. Therefore, a key management protocol is introduced in the IPSec protocol. The Internet key exchange protocol, IKE, can dynamically authenticate IPSec peers and negotiate security services. And the shared key is automatically generated. IPsec-VPN--virtual private network What is VPN--Virtual Private Network VPN role - remote connection through the public network, the private network is linked to the type of VPN: 1, overlay VPN, such as IPsec-VPN 2, peer-to-peer VPN, such as MPLS-VPN can also be divided into Layer 2 VPN and Layer 3 VPN IPsec-VPN is a three-tier VPN IPsec-VPN classification: 1. Site-to-site VPN is also called LAN-to-LAN VPN (requires both sites to have fixed IP) 2. EASY-VPN is also called remote VPN (usually used to connect sites without fixed IP) IPsec- VPN provides three features: 1, authenTIcaTIon certification of each IP packet 2, data integrity to verify data integrity, to ensure that there is no artificial changes in the transmission process 3, confidenTIality (privacy) data packet encryption "knowledge preparation" Before learning IPsec technology, you should first learn the following knowledge: 1. Encryption mechanism 2, DH key exchange algorithm 3, authentication mechanism 4, hash mechanism Encryption mechanism - Cryptography is divided into two categories: Symmetric encryption algorithm - use a key to provide secure protection of information. There is only one key, which is used for encryption, and is also used for decryption features: 1. Fast speed 2, compact ciphertext 3, for the transmission of large amounts of data Symmetric encryption represents: DES, 3DES, AES 3DES--Three keys, encrypted with the first key, decrypted with the second key, and encrypted with the third key Asymmetric encryption --- There is a pair of keys, one is called the public key, and the other is called the private key. If one of them is encrypted, it must be decrypted with another. Features: 1, slow speed 2, cipher text is not compact 3. Usually only used for digital signatures, or encrypt some small files. Representative of asymmetric encryption: RSA, ECC Asymmetric encryption stands for RSA--has a pair of keys, a public key, a private key, private key encryption, public key decryption, or public key encryption, private key decryption Asymmetric encryption can be used in two applications: 1. Public key encryption, private key decryption, encryption 2, private key encryption, public key decryption, digital signature The ideal application method uses asymmetric cryptography to transmit symmetrically encrypted keys or used in digital signatures. Encrypt the actual data with symmetric encryption. The digital signature not only proves the content of the message, but also proves the identity of the sender. Keyed HASH—When encrypting a message digest generated using a key pair, it is called an encrypted message digest. Diffie-hellman key exchange--DH algorithm It is a safe way for the two parties to negotiate a shared key. Use the public key of the other party and the private key of the other to generate a KEY (also called shared secret) that both sides can know. The length of DH group 1 for symmetric encryption is 768 bits (the length of the generated KEY) DH group 2 The length is 1024 bits Authentication mechanism--(here refers to the authentication of the device, not the user's authentication) Modern basic encryption technology relies on a secret known to the intended recipient of the message. The key issue is how to secure the key. 1, username and password 2, OTP (one TIme password) one-time password 3, biometric authentication (fingerprint, eye mask) 4, pre-shared key 5, digital certificate 6, encrypted temporary value Hashing mechanism - used for integrity checking Hash function (that is, HASH)--calculate a large amount of data to obtain a smaller, fixed-length value. Hash is an irreversible function. This means that once the plaintext generates a hash, it is impossible or extremely difficult to convert it from a hash to a plaintext. HASH features: 1, regardless of what data is input, the output is fixed length 2, as long as the input has a slight change, the output will change a lot, that is, the avalanche effect 3, irreversible HASH algorithm: 1, md5 provides 128-bit output md5 is verification, not encryption technology, used to do hash 2, SHA provides 160-bit output HMAC--Use hashed message authentication code, or keyed HASH, is a mechanism for authenticating using HASH. Can be used to authenticate the pre-shared key. -------------------------------------------------- -------------------------------------- The composition of IP sec -- the IPsec protocol set includes three Agreement: 1. internet key exchange (IKE) key exchange protocol The algorithm used by both parties to the protocol, the key, negotiates to establish a ramp parameter between the two peers, and negotiates the completion of the method to encapsulate the data. IKE dynamic, periodically update the key between two PEERs 2, encapsulating secutity payload (ESP) package security load Can authenticate, encrypt, encapsulate, IP protocol number -50, usually use 3DES for encryption. 3, authentication header (AH) Only provide authentication, encapsulation, no encryption, plain text transmission, IP protocol number - 51 Two modes of IPsecVPN -- Algorithms, encapsulation techniques, and keys. This negotiation process is completed by IKE. The IKE negotiation runs in two phases: Phase 1: Establish a secure management connection between two peer devices. There is no actual data to pass this connection. This management connection is used to protect the second phase of the negotiation process. Phase 2: Once the peers have a secure management connection, they can then negotiate the security parameters used to build the secure data connection. This negotiation process is secure and encrypted. After the negotiation is completed, a secure data connection will be formed between the two sites. Users can use these secure data connections to transfer their own data. Phase 1: Establishing ISAKMP SA Negotiation is the following information: 1. Which method is used for authentication between peers, whether it is a pre-shared key or a digital certificate. 2. Which encryption algorithm is used by both parties? 3. Which HMAC mode is used by both parties, whether it is MD5 or SHA 4, and which Diffie-Hellman key group is used by both parties. 5. Which negotiation mode to use (main mode or active mode) 6. Also negotiate the lifetime of the SA The second stage: Establishing IPsec SA negotiation is the following information: 1. Which encapsulation technology is used by both parties, AH or ESP 2. Which encryption algorithm is used by both parties? 3. Which HMAC mode is used by both parties, whether it is MD5 or SHA 4, which transmission mode is used, whether it is tunnel mode or transmission mode 5, and the lifetime of SA is also negotiated. The first phase of the negotiation process has a total of six messages: 1, message 1 and message 2 are used to negotiate encryption mechanism between peers ISAKMP contains the ISAKMP header, SA load, proposed load, conversion load and other fields. In general, the two parties negotiated the use of the dice protocol and encryption method between us. Specifically, it is necessary to agree on four things: encryption mechanism, hash mechanism, DH group, authentication mechanism 2, message 3, and message 4 for exchanging public keys with each other. The peers at both ends first generate their own private key and public key, and also generate a temporary value. Then use Message 3 or Message 4 to exchange the respective public key and temporary values. After the public key is exchanged, each peer first generates a shared secret (using the DH algorithm) according to the public key of the other party and its own private key, and then generates three based on the shared secret, the temporary value of the other party and the self, and the pre-shared key. SKEY: SKEYID_d--This key is used to calculate subsequent IPsec key resources SKEYID_a--This key is used to provide data integrity for subsequent IKE messages and to authenticate SKEYID_e--this key is used to encrypt subsequent IKE messages ISAKMP for messages 3 and 4 contains the following fields: ISAKMP header, key exchange payload (KE), temporary value payload 3, message 5, and message 6 for authentication between two peers. These two messages were performed with SKEYID_e. Encrypted. Each peer generates a hash value based on a large number of Dongdong (including SKEYID-a, pre-shared key, ID), and then sends this value and its own ID (usually IP or hostname) to the other party. Of course, the message 5 or message 6 is used. After each peer receives the ID and hash value of the other party, it first finds the public key of the other party according to the ID of the other party, and then calculates the local hash value. If the local hash value is the same as the hash value of the other party, the authentication succeeds. After this step is completed, the IKE SA is established, and the main mode authentication completes the second phase of the negotiation process. There are three messages in total: 1. The first and second pieces of information are the encapsulation protocols, modes, and encryption algorithms that form the IPsec SA between the two peers. They also need to re-transmit the new public key and temporary values ​​that are regenerated by DH, and other parameters, such as SPI. , ID, etc. 2. The third message is usually sent by the initiator to the responder, which serves as an acknowledgement and is also used to verify the validity of the communication channel. Before the third message is sent, the peers at both ends must first generate a new DH secret with the information related to DH (the new private key and the counterpart public key), and then use this value together with SKEYID_d and some other parameters to generate the final plus. Decrypted KEY. -------------------------------------------------- ------------------------------------------ SA--security association The SA is an agreement established by two communicating entities through negotiation. It determines the IPsec protocol, the transcoding method, the key, and the effective existence time of the key used to protect the security of the data packet. Any IPsec implementation always builds an SA database (SA DB) that maintains the SA records that the IPsec protocol uses to secure packet security. SA is unidirectional--If two hosts (such as A and B) are communicating securely through ESP, then Host A needs to have an SA, SA(OUT), to handle outgoing packets, and also to handle outgoing packets. A different SA is required, that is, SA(IN) is used to process incoming packets. The SA (OUT) of Host A and the SA (IN) of Host B will share the same encryption parameters (such as keys). The SA is also differentiated according to the protocol. If ESP and AH are used simultaneously between the two hosts, different SAs are generated for ESP and AH. SADB--security association database, including IKE and IPsec security information negotiated by both parties SPI--Security Parameter Index, a 32-bit value that identifies the specific security association used to process the packet. Or this is understood to be used to uniquely define a one-way IPsec channel. This number exists in the ESP header and must be consistent at both ends of the channel. SA is divided into two types -- 1. IKE (ISAKMP) SA negotiates the encryption of the IKE data stream and the algorithm for authenticating the peer 2. The IPsec SA negotiates the IKE SA between the algorithm peers that encrypt the IP data stream between the peers. There can only be one IPsec SA between peers. PFS--Performs the forwarding security. It is an attribute that the initiator can provide suggestions to the responder in IKE negotiation. It is an attribute that forces the two parties to generate a new DH secret in the fast mode exchange. This allows the encryption key used to encrypt the data to be generated using the new DH secret. -------------------------------------------------- ------------------------------------------ Configuration example: Steps: 1, configure crypto ACL Configure the stream of interest, the traffic that needs to be encrypted is the stream of interest. 2, establish ISAKMP policy the first phase of the strategy 3, configure IPsec transform set the second phase of the strategy 4, configure crypto map 5, apply crypto map to the interface application under the interface 6, configure interface ACL to determine which traffic is released on the external network interface First, define the flow of interest: Ip access-list extended VPN Permitip 172.16.1.0 0.0.0.255 172.16.2.0 0.0.0.255 Second, IKE first phase cryptoisakmp policy 10 encryption des hash md5 Authentication pre-share group 2 Crypto isakmp key cisco address 202.100.1.2 definition of pre-share key III, IKE second stage Cryptoipsec transform-set MYSET esp-des esp-md5-hmac mode tunnel 4. Map the stream of interest and the transform set to crypto map MYMAP 100 ipsec-isakmp Set peer 202.100.1.2 Set the address of the VPN peer set tranform-set MYSET Set the conversion set Match address VPN binding of the stream of interest and the transform set Five, MAP and interface binding int s0 Crypto map MYMAP Sixth, set the interface to only allow VPN traffic, set the access-list 100 permit udp any eq 500 any eqisakmp Access-list 100 permit esp any any Access-list 100 permit ip 172.16.2.0 0.0.0.255 172.16.1.0 0.0.0.255 Since the ACL will be searched twice, the traffic of the private network will also be released. show crypto isakmp policy Show crypto isakmpsa SA show crypto ipsecsa for the first phase SA show crypto engine connections active show crypto map Crypto ipsec security-association lifetime [seconds|kilobytes] A negotiation time for the second phase, which means how long it takes to renegotiate the key. It is also possible to negotiate how much traffic has been sent. Which value will take effect first. Crytoisakmpkeepalive 10 3 The end of the IPsec channel: When the traffic exceeds the upper limit or the timeout automatically ends the clear crypto isakmp clear the first stage clear crypto sa clear the second stage Clear crypto session In the new version of IOS, use this command to clear the debug crypto isakmp debug crypto ipsec Points to note when configuring IPsec-VPN: 1. Routing 2, interested in traffic 3, strategy 4, call Interface setting ACL: Set the interface to only allow VPN traffic to run, set in the interface Access-list 100 permit udp any eq 500 any eqisakmp access-list 100 permit esp any any or access-list 100 permit ahp any any Note: In the old IOS, after the package is decrypted, it will match the access list again. The new IOS will not, so you should add a new one in the old IOS. Access-list 100 permit ip 192.168.3.0 0.0.0.255 192.168.2.0 0.0.0.255 Routing problems in IPsec: R1 requires a route of 4.4.4.0 R2 requires 4.4.4.0 1.1.1.0 30.0.0.0 route R3 requires 1.1.1.0 4.4.4.0 20.0.0.0 route R4 requires 1.1.1.0 route -------------------------------------------------- ----------------------------------------- --------- -------------------------------------------------- -------------------------------- GRE GRE Generic Routing Encapsulation - A Layer 3 protocol that encapsulates various data packets into IP packets and transmits them over an IP network. That is to say, other IP packets or non-IP packets can be re-encapsulated, and a GRE header and a new IP header are added in front of the original header. Clear text transmission, no security. Protocol number 47 in IP. GRE package format: 20 bytes 4 bytes GRE has good tunneling characteristics. 1. Supporting multi-protocol 2. Supporting multicast defects is an insecure IPsec feature: 1, can provide a secure transmission guarantee 2, but only supports IP, can not support other protocols Tip: In tunnal, after specifying the destination address, as long as there is this address in the local routing table, tunnal will up GRE over IPsec (a highly practical technology, not as troublesome as IPsecVPN) Principle: In the tunnel, first use GRE to encapsulate the data packet into an IP packet, and then encrypt it with IPsec. The default is channel mode. The red part is the encrypted part IPsec can only encrypt IP packets and cannot encrypt non-IP packets. Note the definition of the stream of interest in GRE over IPsec: (All GRE traffic is the stream of interest) access-list 100 permit gre host 202.100.13.3 host 202.100.12.2 The public network address must be defined because when the traffic of interest comes over: 1. Check the route first and enter the tunnel port. 2. After the GRE is packaged, enter the S port and hit the map. After the GRE is encapsulated, the external IP address uses the public network address, so the traffic of interest must be defined as the public network address. Because the ACL is checked twice on the interface, if the ACL is placed on the physical interface, the ESP and GRE traffic must be released at the same time, and the isakmp negotiation traffic is also available. GRE over IPsec technology recommends using transport mode because the communication point is equal to the encryption point test: First, configure tunnel interface tunnel 1 Tunnel source 202.100.1.1 tunnel destination 202.100.1.2 tunnelgreip Ip address 12.1.1.1 Second, run the routing protocol routereigrp 90 Network 172.16.1.0 0.0.0.255 network 12.1.1.0 0.0.0.255 Third, start to configure IPsec, first define the stream of interest: (note the definition here) ip access-list extended VPN Permitgre any any Fourth, IKE first phase cryptoisakmp policy 10 encryption des hash md5 Authentication pre-share group 2 Crypto isakmp key cisco address 202.100.1.2 definition of pre-share key V. IKE second stage Cryptoipsec transform-set MYSET esp-des esp-md5-hmac mode tunnel 6. Map the stream of interest and the transform set to crypto map MYMAP 100 ipsec-isakmp Set peer 202.100.1.2 Set the address of the VPN peer set tranform-set MYSET Set the conversion set Match address VPN binding of the stream of interest and the transform set Seven, MAP and interface binding int s0 Crypto map MYMAP Eight, set the interface only allows to run VPN traffic, set in the interface in the direction of the physical interface -- Access-list 100 permit udp any eq 500 any eqisakmp access-list 100 permit esp any any access-list 100 permit gre any any -------------------------------------------------- --------------------------------------- ----------- -------------------------------------------------- ---------------------------- Disadvantages of site-to-site VPN: 1. There must be fixed public IP on both ends. 2. The configurations on both ends are too complicated. 2500 puffs disposable vape pen are so convenient, portable, and small volume, you just need to take them disposable vape 2500 puffs,disposable vape pen 2500 puffs,2500 puff vape pen,e-cigarette 2500 puffs,2500 puffs vape bar Ningbo Autrends International Trade Co.,Ltd. , https://www.ecigarettevapepods.com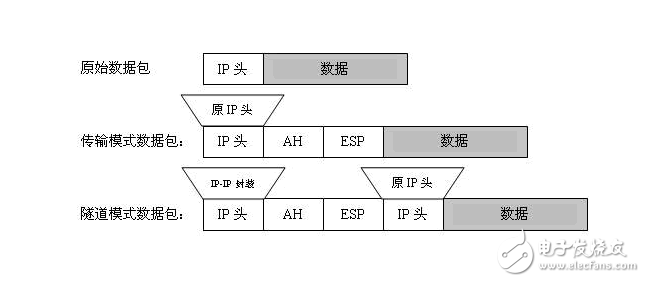
out of your pocket and take a puff, feel the cloud of smoke, and the fragrance of fruit surrounding you. It's so great.
We are China's leading manufacturer and supplier of disposable vape puff bars, disposable vape 2500 puffs,disposable vape pen 2500 puffs,
e-cigarette 2500 puffs,2500 puffs vape bar, and e-cigarette kit, and we specialize in Disposable Vapes, e-cigarette vape pens, e-cigarette kits, etc.